Creating Firewall Rules
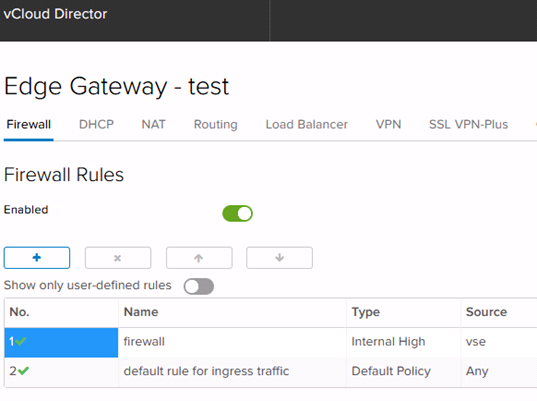
To create a Firewall rule, navigate to the Edge Gateway, right-click and select “Edge Gateway Services”. Then select the Firewall tab. Click the “+” symbol to add a rule, and the “x” symbol to delete a rule. Select a rule and use the “↑” and “↓” icons to change rule order.
The Firewall is enabled by default, and denies all traffic by default. To allow traffic, both outbound and inbound rules are necessary. See below for examples of both inbound and outbound rules.
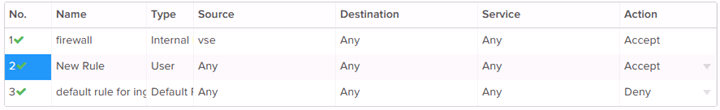
Once the firewall rule is created, it will appear in the rules list as “New Rule”.
Once the rule is created, the user will need to edit the rule to perform its intended function by editing the Source, Destination, Service and Action fields.
Editing Firewall Rules
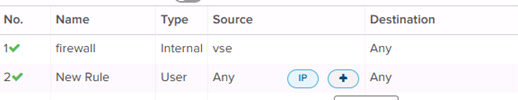
To edit the Source and Destination fields for a Firewall Rule, mouse over the field and select “IP” for IPv4 definition, or the “+” icon to set the field to a network object.
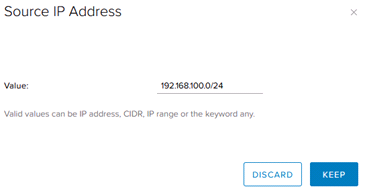
To add an IPv4 Source or Destination range, enter the appropriate range in the “Value” field in the popup as shown below, and select “Keep”.
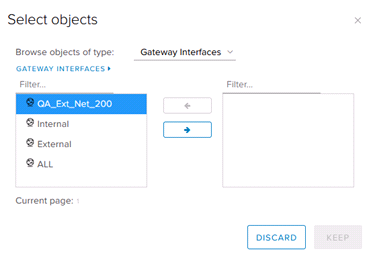
A network object can also be used as a Source or Destination. Select the appropriate type from the dropdown menu, then select the specific relevant object. Select the “→” icon to add the object to the rule. A summary of network object types is shown below.
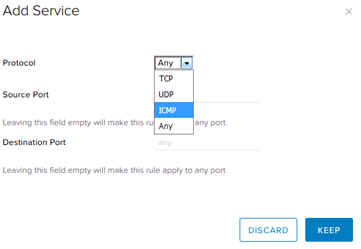
To edit the Firewall Rule’s Service, select the “+” icon to select a service (network protocol and port). To edit the Action (Accept or Deny), select the appropriate action from the dropdown menu.
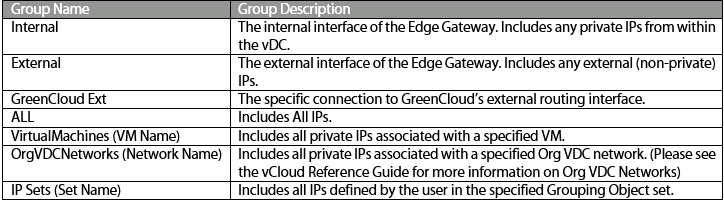
Networking Objects
The chart below shows a description of each Network Object available by default in the Edge Gateway Firewall Rule editor. Note that manually-defined objects are available from the Grouping Objects tab.
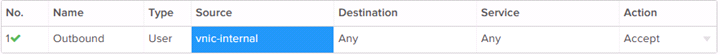
Firewall Rule Example: Allow All Outbound
This Firewall rule allows all outbound traffic from an internal subnet.
The “vnic-internal” object refers to any private IP on the Edge Gateway’s internal interface. The “any” keyword covers any value for the relevant fields. The action is set to “Allow”, which overrides the default “Deny” action.
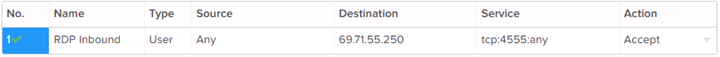
Firewall Rule Example: Allow Specific Inbound
This firewall rule allows traffic from any source to access the external IP at a specific port.
The port should match a port defined by a Port DNAT rule. See NAT Rule Management for how to set up a corresponding NAT rule.
NAT rules and Firewall rules work together to route traffic across the Edge Gateway. Both are necessary for normal traffic. GreenCloud support is always available for assistance troubleshooting NAT rule interactions.
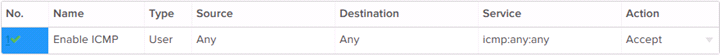
Firewall Rule Example: Allow ICMP
This Firewall Rule explicitly allows ICMP traffic across to an internal server, which will enable ping traffic. Please note that ICMP ping response is also disabled by default on GreenCloud VMs, so it may be necessary to verify that ICMP is also on for the target server in order to successfully ping.
This rule will allow ping traffic to flow to the target internal IP from an external source.