Please note that an IPSEC VPN capable device must be installed at the remote site in order to configure this type of VPN. If there is no VPN capable device at the remote site, no site-to-site VPN can be deployed on the Edge Gateway.
1. Begin VPN Creation
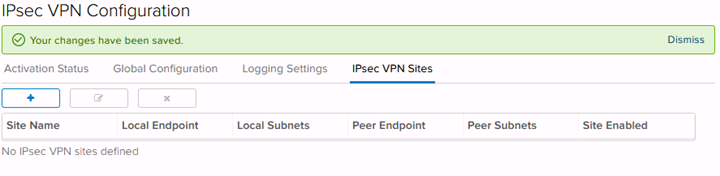
The Edge Gateway can also negotiate and manage VPN connections. To create a VPN, navigate to the Edge Gateway, right-click and select “Edge Gateway Services”. Then select the VPN tab, followed by “IPSEC VPN Sites”. Click the “+” icon to begin the configuration process.
2. VPN Configuration
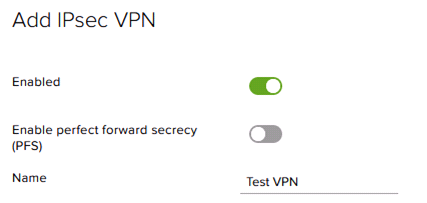
Switch the “Enabled” field to On, and name the VPN and specify that the VPN will go to a remote network, as shown below. Set the PFS switch to match the target device (certain devices do not support PFS).
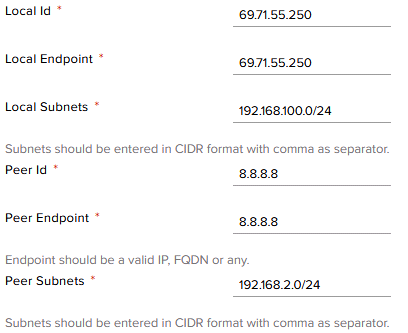
Enter the Local ID and Endpoint, both of which should be the Edge Gateway’s external IP depending on the ID expected by the remote site. Then enter the Local Subnets, which will be connected to the Peer Subnets. Add the Peer ID and Endpoint, which should both be the external IP of the destination device. Then add the Peer Subnet, which should be the internal network at the remote site on which the client devices are addressed. Please note that the subnets are not allowed to duplicate any existing subnet on either site.
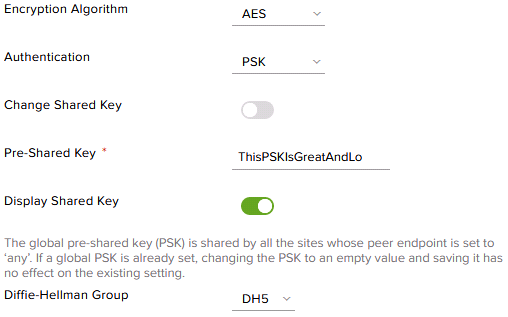
Select the Encryption Algorithm and Authentication method. If a PSK is established, enter it in the Pre-Shared Key field. Select the correct Diffie-Helllman group for the remote device’s configuration. Please note that Pre-Shared Keys for VPNs on Edge Gateways must be a minimum of 32 characters in length. Ensure that the networking information is correct, then select “Keep” to complete the configuration.
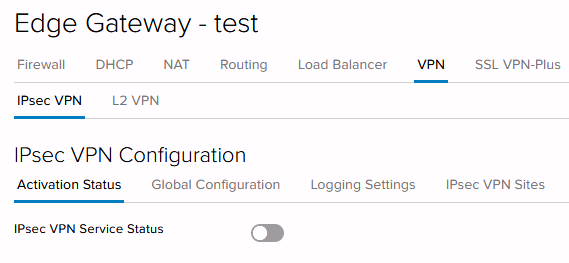
After saving, navigate back to “Activation Status” under the the “IPsec VPN” Tab. The VPN service (“IPSEC VPN Service Status” switch under Activation Status) is disabled by default to consume resources. Switch this on after adding a VPN.
VPN Firewall Rules
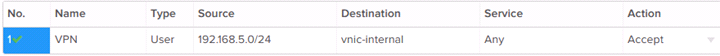
An additional firewall rule will be necessary in order to pass traffic across the VPN. Without this Firewall rule no traffic will be allowed and both endpoints will report the VPN as down.
This Firewall rule allows traffic from the remote/peer subnet (see the configuration above) to flow to any internal/private subnet, which includes the internal network on which the client’s VMs should be addressed.
At this point the corresponding settings must be entered on the remote network device in order to begin VPN negotiation. Note that the Edge Gateways on vCloud follow the VMware default configuration listed in this KB article. Logs and further support may be obtained by contacting GreenCloud Support.
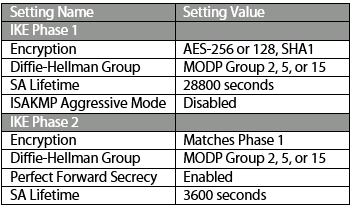
VPN Configuration Settings
Please see below for a list of VMware Edge Gateway default settings for VPNs.