Access rules allow traffic to flow across the ASAv. Since all Green Cloud ASAv’s have a default policy to deny traffic, any traffic flow must be explicitly allowed. This includes any inbound traffic, any traffic across internal subnets, and any VPN traffic.
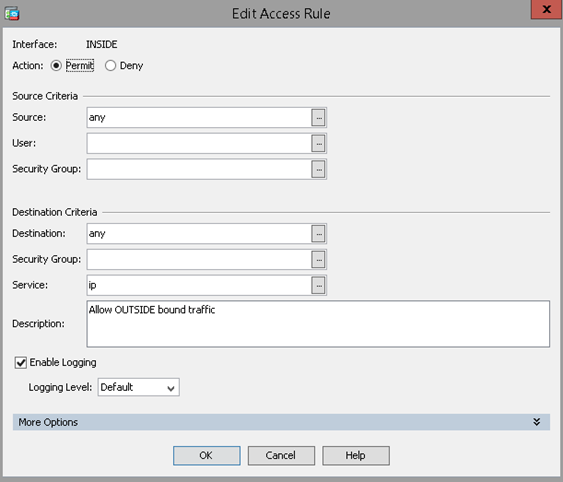
Firewall Rule Example: Allow outbound traffic
The following Access Rule allows any traffic from the INSIDE interface to flow to any destination. It is applied on the INSIDE interface and pertains exclusively to IP traffic. This is a very basic firewall rule which should be present on all GreenCloud ASAv’s.
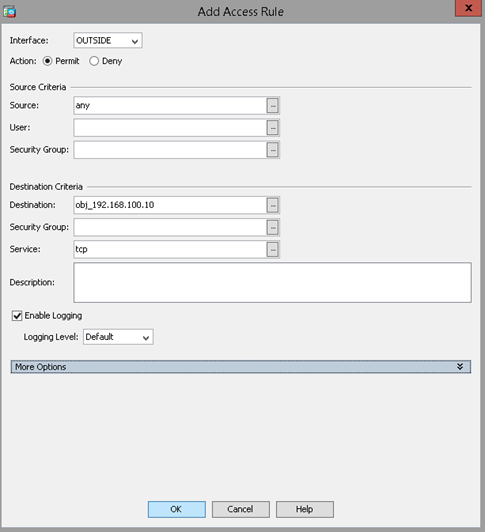
Firewall Rule Example: Allow Inbound Traffic to an IP
The following Access Rule allows any traffic from the OUTSIDE interface to flow to a specific internal IP. This rule is necessary for external access to a server, such as through RDP. It explicitly allows TCP traffic, but denies all other traffic through the default deny policy.
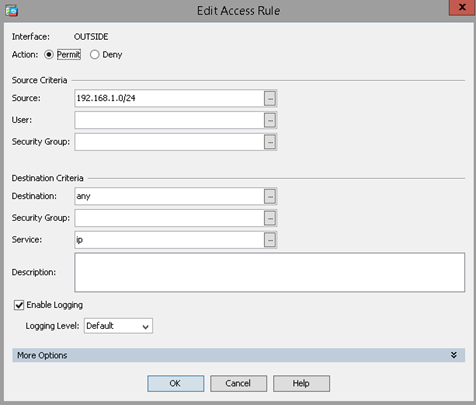
Firewall Rule Example: Allow Traffic Across Internal Subnets (VPN Access Rule)
This firewall rule allows traffic from the OUTSIDE interface, which comes from an internal VPN-connected subnet, to flow to any destination. It specifically allows that traffic to flow to the other internal subnets on the INTERNAL interface of the ASAv. This will allow traffic from VPNs to route properly, but should only be necessary if the “Bypass access lists” checkbox is selected for VPNs.