With the FortiOS intrusion prevention system (IPS), you can detect and block network-based attacks. You can configure IPS sensors based on IPS signatures, IPS filters, outgoing connections to botnet sites, and rate-based signatures. FortiOS includes eight preloaded IPS sensors:
- all_default
- all_default_pass
- default
- high_security
- protect_client
- protect_email_server
- protect_http_server
- wifi-default
You can customize these sensors, or you can create your own and apply it to a firewall policy. The Botnet C&C section consolidates multiple botnet options in the IPS profile. This allows you to enable botnet blocking across all traffic that matches the policy by configuring one setting in the GUI.
Go to Security Profiles > Intrusion Prevention, Edit an existing sensor, or create a new one, and set Scan Outgoing Connections to Botnet Sites to Block or Monitor.
Click Apply. Botnet C&C is now enabled for the sensor. Add this sensor to the firewall policy. The IPS engine will scan outgoing connections to botnet sites. If you access a botnet IP, an IPS log is generated for this attack. Go to Log & Report > Intrusion Prevention to view the log.
Botnet C&C domain blocking
Go to Security Profiles > DNS Filter. Edit an existing filter, or create a new one. Enable Redirect botnet C&C requests to Block Portal. Then add this filter profile to a firewall policy.
Botnet C&C URL blocking
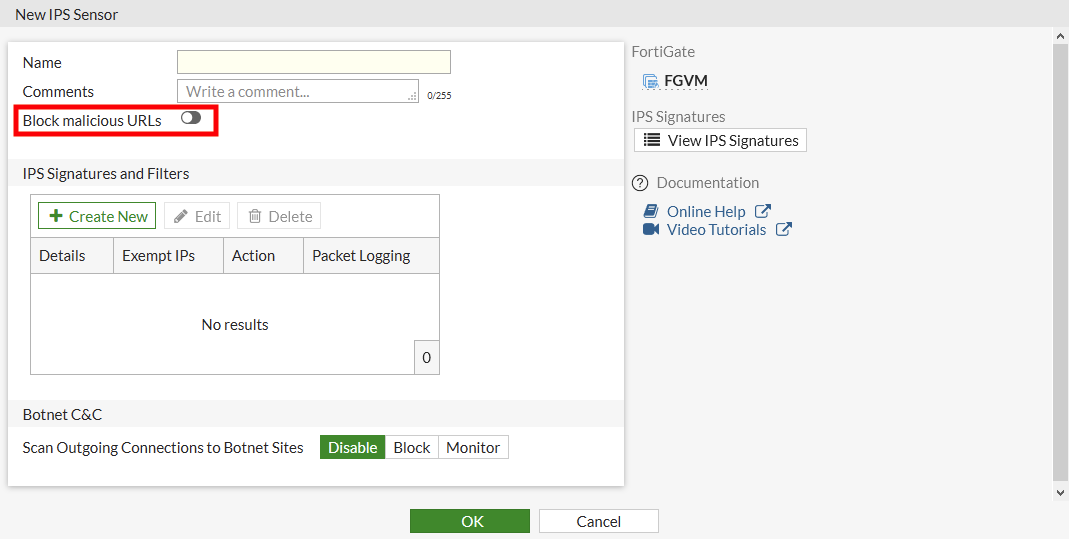
Go to Security Profiles > Intrusion Prevention. Edit an existing sensor, or create a new one. Enable Block malicious URLs. Then add this sensor to a firewall policy.
Botnet C&C signature blocking
Go to Security Profiles > Intrusion Prevention. Edit an existing sensor, or create a new one. In the IPS Signatures section, click Create New. Set Type to Signature and select the signatures you want to include from the list. Add this sensor to a firewall policy to detect or block attacks that match the IPS signatures.



